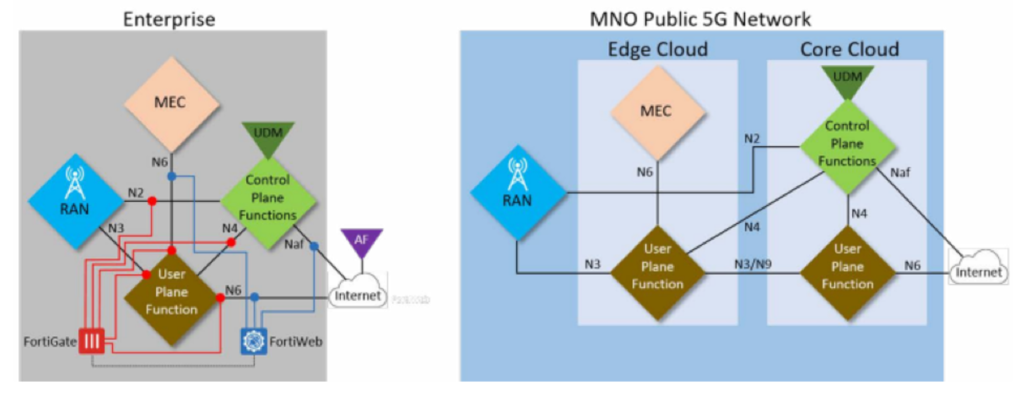
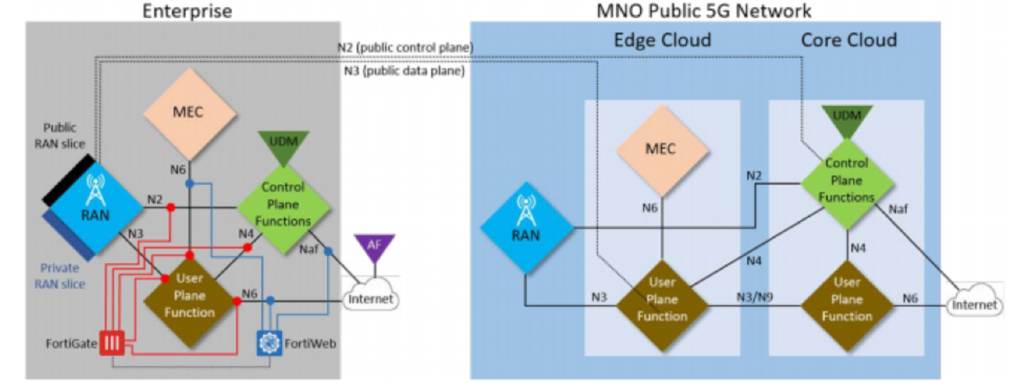
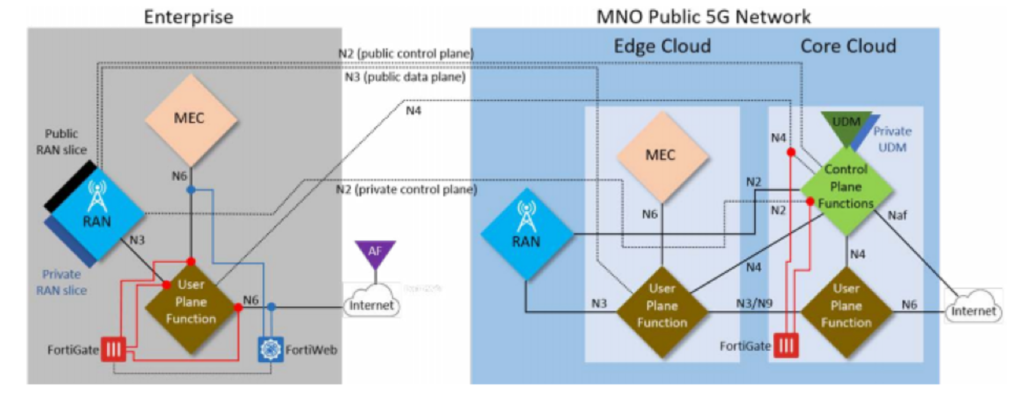
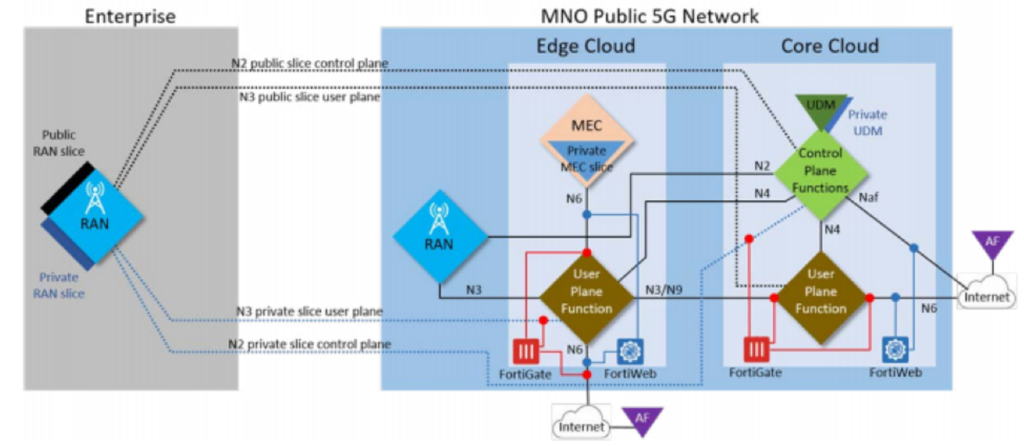
Cybersecurity Posts
Read Industry Highlights

Featured Post from Venturebeat

GenAI revolution is here, but is your cloud network ready to embrace it

GenAI development should follow Secure By Design Principle

CISOS guide to 2024: Top 10 Cyber security trends

AI Security Overview: AI Exchange