The 5G revolution promises lightning-fast speeds and ubiquitous connectivity, but with this technological leap comes a heightened security imperative. Traditional deployment methods, often manual and time-consuming, leave vulnerabilities exposed. Enter Zero Touch principles, a paradigm shift that automates and secures 5G network deployment, building a fortress from the ground up.
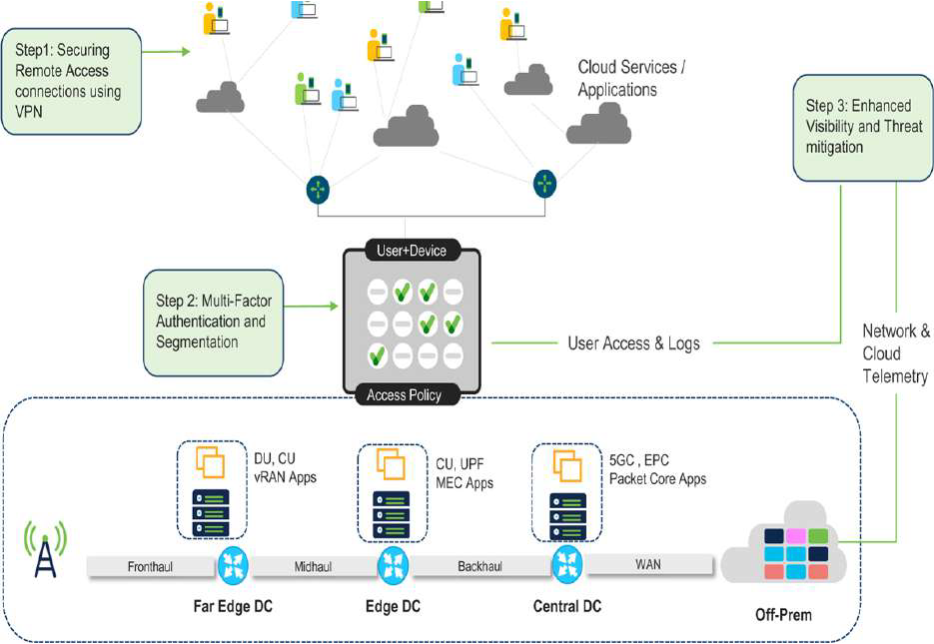
The diagram illustrates the interconnected elements of Zero Touch security. Let’s delve into these checkpoints, weaving a tapestry of impenetrable defense:
1. Securing the First Touchpoint: Remote User VPN
As the very first interaction, remote user access demands robust security. A Zero Touch approach prioritizes Remote User VPN, creating a secure tunnel for administrators to access and configure network elements remotely, eliminating the need for physical presence and potential security loopholes.
2. Multi-Factor Authentication: Layering the Defense
Beyond passwords, Multi-Factor Authentication (MFA) adds an extra layer of protection. Biometric verification or one-time codes act as additional hurdles for unauthorized access, significantly reducing the risk of compromised credentials.
3. Device Profiling: Knowing Your Friends (and Foes)
Zero Touch doesn’t treat all devices equally. Device Profiling automatically identifies and categorizes connected devices, distinguishing authorized equipment from potential intruders. This granular understanding allows for tailored security policies and immediate action against suspicious devices.
4. Micro-Segmentation: Building Walls Within Walls
The network itself becomes a fortress with Micro-Segmentation. This virtualizes the network, creating isolated zones for different functions and access levels. Even if one zone is breached, the damage is contained, preventing lateral movement and protecting critical assets.
5. Endpoint Protection: Shielding the Outposts
Zero Touch extends its reach to the endpoints. Endpoint Protection software automatically deploys and updates security solutions on connected devices, ensuring real-time protection against malware and other threats, even on the network periphery.
6. Granular Visibility and Immediate Quarantine:
Constant vigilance is key. Zero Touch prioritizes Granular Visibility, providing administrators with a real-time, comprehensive view of network activity. This holistic understanding allows for Immediate Quarantine of suspicious devices or activities, nipping threats in the bud before they can spread.
7. DNS Security: Guarding the Domain Names
The Domain Name System (DNS) acts as the internet’s address book. DNS Security safeguards this critical infrastructure, preventing attackers from redirecting traffic or injecting malicious content. This protects both users and devices from falling prey to online traps.
8. Securing the Smallest Soldiers: IoT Device Authentication and Authorization
The ever-growing army of IoT devices necessitates robust identification and access control. IoT Device Authentication and Authorization ensures only authorized devices can connect and operate, preventing rogue elements from infiltrating the network and potentially disrupting critical operations.
Zero Touch: More Than Just Speed
While Zero Touch principles streamline deployment, their true value lies in their inherent security. By automating critical security measures, Zero Touch builds a robust defense from the very first connection, minimizing human error and proactively thwarting potential threats. This comprehensive approach ensures that the 5G revolution unfolds not just at breakneck speed, but with unwavering security as its foundation.

